DDoS Protection
A Distributed Denial of Service (DDoS) attack can be used to make websites and other online resources unavailable by overwhelming it with traffic from multiple sources.
Get protectionHow DDoS protection works
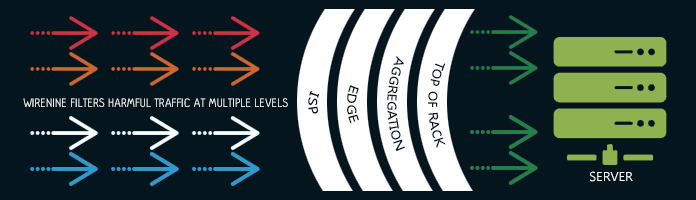
DDoS mitigation service
As DDoS attacks continue to be on the rise, so do financial and brand risks for online businesses. WireNine's DDoS protection offers you peace of mind knowing that we are watching over the network traffic and taking action against attacks when they happen.
Our automated rule sets, combined with our highly skilled engineering staff and technical support teams, work in concert to deliver a worry-free hosting experience. We keep your services online during attacks and save you the high added cost of some other providers.
DDOS PROTECTION AGAINST VARIOUS TYPES OF DDOS ATTACKS:
UDP BASED
- UDP Flood
- Fragmentation
- DNS Flood
- VoIP Flood
- Media Data Flood
- Non-Spoofed UDP Flood
TCP BASED
- SYN Flood
- SYN-ACK Flood
- ACK & PUSH ACK Flood
- Fragmented ACK
- RST or FIN Flood
- Synonymous Flood
- Fake Session
- Session Attack
- Misused Application
ICMP BASED
- ICMP Flood
- Fragmentation
- Ping Flood
- Fragmented ACK
- RST or FIN Flood
- Synonymous Flood
- Fake Session
- Session Attack
- Misused Application